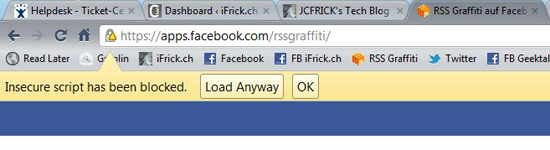
 Seit der letzten Beta Version block der Google Chrome Browser bestimmte Javasacripts. Wird auf einer HTTPS Seite eine Javascript aufgerufen welches nicht SSl verschlüsselt läuft, wird dieses geblockt. Wer zum Beispiel Facebook via SSL Verbindung aufruft, merkt das schnell da viele Apps unverschlüsselte Javascripts auszuführen versuchen. Google schreibt dazu:
Seit der letzten Beta Version block der Google Chrome Browser bestimmte Javasacripts. Wird auf einer HTTPS Seite eine Javascript aufgerufen welches nicht SSl verschlüsselt läuft, wird dieses geblockt. Wer zum Beispiel Facebook via SSL Verbindung aufruft, merkt das schnell da viele Apps unverschlüsselte Javascripts auszuführen versuchen. Google schreibt dazu:
When a website is secured via HTTPS, the web site designer must also ensure that all of the scripts used by the page will be delivered in the same secure manner as the main page itself. The same requirements also apply to the plugins and external CSS stylesheets used by the page, as these have the same considerations as javascript.
When this is not the case (sometimes called a “mixed script” situation), visitors to the site run the risk that attackers can interfere with the website and change the script so as to serve their own purposes.
Traditionally, browsers have run the mixed script, genuine or not, and notified you after-the-fact by a broken lock icon, a dialog box, or a red https:// in the location bar (in the case of Google Chrome). The problem with this approach is that by the time the script has run, it is already too late, because the script has had access to all of the data on the page.
Google Chrome now protects you by refusing up-front to run any script on a secure page unless it is also being delivered over HTTPS. Data on the page remains secure even in the presence of an attacker, but the downside is that this may cause pages to display improperly. You may wish to let the website owner know that their site is not properly secured. (Note that a poorly-written extension can also sometimes cause this).
You can bypass this protection by clicking “Allow Anyway”, in which case Google Chrome will refresh the page and load the insecure content. You will then see an https:// displayed in red in the location bar indicating that the page could not be secured.